Cybersecurity is the shielding of internet-connected (online ) systems such as hardware, software (operating systems) and data from cyberthreats. The practice is used by particular individuals and enterprises to protect against unauthorized access to data centers and other computerized (programmed) systems.
What are the different types of cybersecurity threats?
The process of holding up with new technologies, security trends and threat intelligence is a tough task. It is necessary in order to protect information and other assets from cyberthreats, which take many forms. Types of cyberthreats include:
Malware- is a form of malicious software in which any file or program can be used to harm a computer user. This includes worms, viruses, Trojans and spyware.
Ransomware- is another type of malware. It involves an attacker locking the victim’s computer system files — typically through encryption — and demanding a payment to decrypt and unlock them.
Social engineering- is an attack that relies on human interaction to trick users into breaking security procedures to gain sensitive information that is typically protected.
Phishing- is a form of social engineering where fraudulent email or text messages that resemble those from reputable or known sources are sent. Often random attacks, the intent of these messages is to steal sensitive data, such as credit card or login information.
Spear phishing- is a type of phishing attack that has an intended target user, organization or business.
Insider threats are security breaches or losses caused by humans — for example, employees, contractors or customers. Insider threats can be malicious or negligent in nature.
Distributed denial-of-service (DDoS) attacks are those in which multiple systems disrupt the traffic of a targeted system, such as a server, website or other network resource. By flooding the target with messages, connection requests or packets, the attackers can slow the system or crash it, preventing legitimate traffic from using it.
Advanced persistent threats (APTs) are prolonged targeted attacks in which an attacker infiltrates a network and remains undetected for long periods of time with the aim to steal data.
Man-in-the-middle (MitM) attacks are eavesdropping attacks that involve an attacker intercepting and relaying messages between two parties who believe they are communicating with each other.
Other common attacks include botnets, drive-by-download attacks, exploit kits, malvertising, vishing, credential stuffing attacks, cross-site scripting (XSS) attacks, SQL injection attacks, business email compromise (BEC) and zero-day exploits.

What are the elements of cybersecurity?
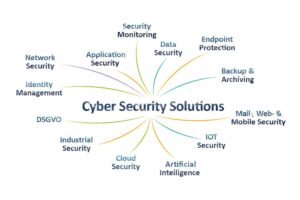
1.Security Monitoring-is the automated process of collecting and analyzing indicators of potential security threats, then triaging these threats with appropriate action.
2.Data security-is the process of safeguarding digital information throughout its entire life cycle to protect it from corruption, theft, or unauthorized access.
3.Endpoint protection-involves monitoring and protecting endpoints against cyber threats. Protected endpoints include desktops, laptops, smartphones.
4.Backups & Archiving-A backup is a copy of your current data that you use to restore original data if it’s ever damaged.An archive is historical data you must keep long-term retention reasons, such as compliance.
5.Mail Web & Mobile Security-To protect online link saved password in mobile and computer.
6.Iot Security-IoT is the act of securing Internet devices and the networks they’re connected to from threats and breaches by protecting, identifying, and monitoring risks all while helping fix vulnerabilities from a range of devices that can pose security risks to your business.
7.Artificial Intelligence-is the simulation of human intelligence processes by machines, especially computer systems. Specific applications of AI include expert systems, natural language processing, speech recognition and machine vision.
8.Cloud Security-Cloud security is a discipline of cyber security dedicated to securing cloud computing systems. This includes keeping data private and safe across.
9. Industrial Security-Cybersecurity for Industry enables continuously monitored, integrated, and multi-layered security as an important basis for industrial automation.
10-Dsgvo-General Data Protection Regulation (GDPR) ·
11. Identify Managment-Identity management (IdM), also known as identity and access management (IAM) ensures that authorized people – and only authorized people – have access to the technology resources they need to perform their job functions.
12-Network Security-Network security is any activity designed to protect the usability and integrity of your network and data.
13. Application Security –Application security is the process of developing, adding, and testing security features within applications to prevent security vulnerabilities against threats.
